Continuing to formalize channels between different sector actors, governments, and legislation enforcements, while nonetheless preserving the decentralized nature of copyright, would advance quicker incident response and also enhance incident preparedness.
enable it to be,??cybersecurity steps may develop into an afterthought, specially when companies deficiency the funds or staff for this kind of measures. The challenge isn?�t one of a kind to those new to organization; on the other hand, even properly-founded firms may well Permit cybersecurity tumble into the wayside or may well deficiency the education to be familiar with the quickly evolving menace landscape.
and you will't exit out and return or you get rid of a lifetime and also your streak. And not long ago my Tremendous booster is not displaying up in each degree like it must
Obviously, this is an incredibly lucrative venture with the DPRK. In 2024, a senior Biden administration Formal voiced concerns that close to 50% on the DPRK?�s overseas-forex earnings came from cybercrime, which includes its copyright theft routines, as well as a UN report also shared promises from member states the DPRK?�s weapons system is largely funded by its cyber operations.
However, factors get challenging when a single considers that in The usa and most nations, copyright remains to be largely unregulated, and also the efficacy of its current regulation is frequently debated.
These risk actors have been then capable to steal AWS session tokens, the short term keys that allow you to ask for short term qualifications on your employer?�s AWS account. By hijacking Energetic tokens, the attackers were in the position to bypass MFA controls and achieve access to Safe and sound Wallet ?�s AWS account. By timing their efforts to coincide While more info using the developer?�s standard perform several hours, Additionally they remained undetected till the particular heist.
 Shaun Weiss Then & Now!
Shaun Weiss Then & Now! Barry Watson Then & Now!
Barry Watson Then & Now!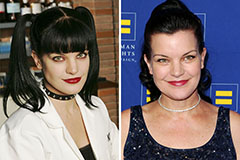 Pauley Perrette Then & Now!
Pauley Perrette Then & Now! Andrew McCarthy Then & Now!
Andrew McCarthy Then & Now! Christy Canyon Then & Now!
Christy Canyon Then & Now!